CMMC 2.0 Scope: How Contractors Can Adapt?

The Department of Defense has over 300,000 contractors, each posing multiple potential cybersecurity challenges. The Department of Defense (DoD) released version 2.0 of the Cybersecurity Maturity Model Certification (CMMC), which includes significant changes to the CMMC scope of the certification. The updates aim to strengthen cybersecurity across the defense industrial base (DIB) by streamlining the CMMC model in the previous version, 1.0. As a result, defense contractors must adapt to these changes and meet the new requirements once the model becomes mandatory compliance.
Understanding the CMMC 2.0 Scope Changes:
The CMMC scope of CMMC 2.0, also known as the Cybersecurity Maturity Model Certification 2.0, primarily revolves around cybersecurity practices and controls that handle Federal Contract Information or FCI and/or Controlled Unclassified Information (CUI).
Here’s a more detailed breakdown of its scope:
-
Defense Industrial Base (DIB):
CMMC 2.0 applies to organizations within the DIB supply chain. This includes defense contractors, suppliers, subcontractors, and other entities involved in supporting the U.S. Department of Defense (DoD) through contracts or partnerships.
-
Information Protection:
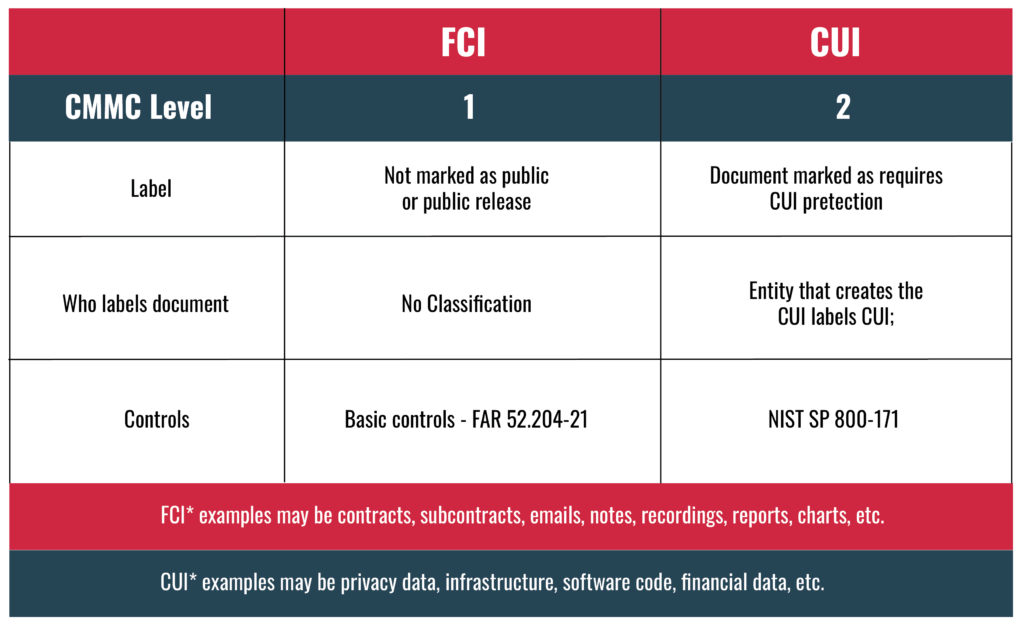
The central focus of CMMC 2.0 is the protection of Controlled Unclassified Information (CUI) and Federal Contact Information (FCI). CUI data, while not classified, can be critical or non-critical and is vital for national security that requires safeguarding with additional controls based on NIST standards. FCI and CUI can encompass a wide range of data, including technical specifications, design drawings, proprietary information, and other critical documents. Some of the examples of FCI and CUI are highlighted in the below table:
-
Cybersecurity Practices and Controls:
Within the CMMC scope of CMMC 2.0 scope, organizations must implement specific cybersecurity practices and controls. These practices cover various aspects of cybersecurity, such as access control, incident response, encryption, network security, and more. The goal is to ensure that organizations handling FCI and CUI have robust cybersecurity controls in place to protect information.
-
Maturity Levels and Modular Approach:
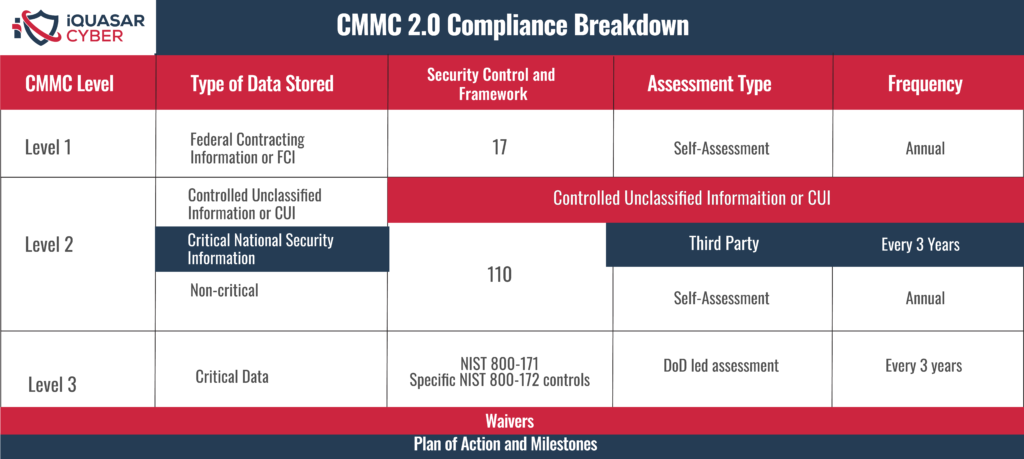
CMMC 2.0 introduces a sliding scale of maturity levels, allowing organizations to tailor their cybersecurity efforts more precisely to their specific needs. It also adopts a modular approach, enabling organizations to focus on and assess individual domains and practices within the framework.
-
Assessment and Certification:
Organizations within the CMMC scope of CMMC 2.0 are subject to assessments to evaluate their cybersecurity maturity and compliance with the framework’s requirements. Certification at the appropriate level of maturity is necessary for continued involvement in DoD contracts and projects.
-
Evolution and Updates:
The CMMC 2.0 operating model allows for greater flexibility in implementation and is set to evolve and adapt to the changing cybersecurity landscape. It may undergo updates and refinements to address emerging threats and industry feedback in the future.
-
Plan of Action & Milestones (POA&M):
CMMC 2.0 permits companies to utilize Plans of Action and Milestones (POA&M) to attain certification demonstrating a commitment to achieve full compliance within a defined timeline. DoD aims to outline specific cybersecurity practices as the fundamental criteria contractors must fulfill before a contract award while allowing contractors to meet the remaining requirements within a clearly defined timeline.
Strategies for Navigating the Updated CMMC Scope:
-
Start Early:
Don’t wait until the last minute to prepare for CMMC 2.0 certification. Allow yourself ample time to assess your cybersecurity posture, do a thorough gap analysis, and implement necessary improvements.
-
Conduct a Thorough Risk Assessment:
To determine where you stand regarding compliance, perform a comprehensive risk assessment, and identify potential vulnerabilities to develop a plan to address them.
-
Prioritize Remediation Efforts:
Based on the results of your risk assessment, prioritize remediation efforts. Focus first on high-risk areas and work your way down to lower-risk ones.
-
Train Employees:
Employee education and awareness are critical components of cybersecurity. Create training programs specifically designed for your organization’s unique needs. Educate employees about the risks associated with cyber-attacks and how they can contribute to preventing them.
-
Partner with Third-Party Providers:
Consider partnering with third-party providers specializing in CMMC 2.0 compliance. These partners can assist with the CMMC’s journey, from risk assessments to remediation efforts and CMMC certification.
-
Communicate with Suppliers and Subcontractors:
Make sure your suppliers and subcontractors understand the new CMMC 2.0 requirements. Provide clear instructions on what you expect from them regarding cybersecurity controls.
-
Embrace Automation:
Utilize automated tools and technologies to streamline your cybersecurity operations. Automation can significantly reduce manual tasks, freeing staff to concentrate on higher-level security functions.
-
Stay Informed:
Keep abreast of the latest news and updates related to CMMC 2.0. Attend industry events, join webinars, and participate in online forums.
Cybersecurity Maturity Model Certification (CMMC) is vital to contract awards from DoD and securing the defense industrial base (DIB) supply chain. With the introduction of CMMC 2.0, defense contractors must comply with stricter cybersecurity requirements to ensure the safety of sensitive data once CMMC becomes regulatory compliant. However, navigating the updated CMMC scope and implementing the necessary measures can be challenging without proper guidance. That’s where we come in. Our team of experts at iQuasar Cyber, Inc. has extensive experience helping organizations prepare for CMMC compliance. To learn more about our services and how we can support your organization in achieving CMMC compliance: