Identity and Access Management (IAM)
Is your staff provided with secure access to the right resources as and when they need them? Do you have control over who has access to what in terms of data, networks, software applications, and other corporate information?
With an Identity and Access Management (IAM) solutions, you can empower your staff to access the right resources quickly and securely. From real-time access monitoring of user activity to ensuring regulatory compliance – all while keeping your critical data safe – IAM offers a perfect balance between user experience, safety, accessibility, and productivity.

Role-Based Access Control
Get granular control over user access by implementing Role-Based Access Control (RBAC) and empower users based on their responsibilities while keeping user accounts secure with minimum of effort
User and Entity Behavior Analytics (UEBA)
Utilize IAM processes to augment behavioral analytics. Monitor and action human and non-human behavior anomalies in your organization by collecting and organizing data for user and non-user entities, to integrate data into security systems to prevent cyber attacks
Application integration
Integrate IAM systems with enterprise applications to automate the creation, management, and deactivation of digital identities. Embed IAM processes in to business processes to provide the right access to systems and data
Access Governance - Certifications and Remediations
Get a 360 degrees view of the user life cycle management process and access certifications. Provide on time remediations to reduce risk and streamline compliance. Prepare on-demand user access reports in a few minutes to satisfy internal and external auditor requirements
Privileged Access Management
Implement stronger controls for privileged users who manage critical systems and data to protect your organization’s crown jewels
User Experience, Authentication, and Single Sign-On
Improve the security and efficiency of your organization with a standardized approach to authentication, and enhanced user experience. Introduce risk based authentication to prevent unauthorized access
Provisioning and De-Provisioning Automation
Automate standard provisioning and de-provisioning to improve efficiency and lower IAM costs. Minimize access risk by automation and on-demand IAM controls
Access Request Automation
Automate access request and approval from as a part of the IAM joiner process. Provide birthright access from Day one of Onboarding without any manual intervention
Our IAM Solutions
IAM Tool integration
Integrate IAM systems and applications with Sailpoint’s IdentityIQ to automate the creation, management, and deactivation of digital identities and provide precise access control to systems and data.
Authentication
Improve the security and efficiency of your systems with a standardized and centralized approach in place for authenticating user access to enterprise resources.
Identity Provisioning and Administration
Stay in control of your user accounts by creating, modifying, and deleting them as necessary. Manage access rights and permissions to protect against unauthorized use or data breaches
Business Intelligence and Auditing
Safeguard your business with detailed audit logs that can help you track user activity and stay ahead of potential risks. Uncover policy breaches instantly to ensure timely corrective measures are taken, protecting all assets from preventable harm
Role-Based Access Control
Get granular control over user access by implementing Role-Based Access Control (RBAC) and empower users based on their responsibilities while keeping user accounts secure
Single Sign-On
Lower costs and create an improved user experience by eliminating multiple logins and passwords through a single streamlined solution, allowing easy and secure management of authentication across multiple systems
Multi-factor authentication
Protect your confidential data from intrusive outsiders with a variety of authentication solutions. Strengthen defenses against unauthorized access – go passwordless, deploy biometrics, and secure accounts through multi-factor verification
Access Control
Secure access to sensitive information and resources by managing user access via attributes, roles, and privileges. Keep unauthorized users out while making sure authorized ones have just the right amount of control at the right time
Why Do Businesses Need IAM Solutions
Cost Reduction
Cost Reduction
Improved User Experience
Improved User Experience
Risk Reduction
Risk Reduction
Increase Efficiency and Standardization by automation
Increase Efficiency and Standardization by automation
Meet Compliance Requirement
Meet Compliance Requirement
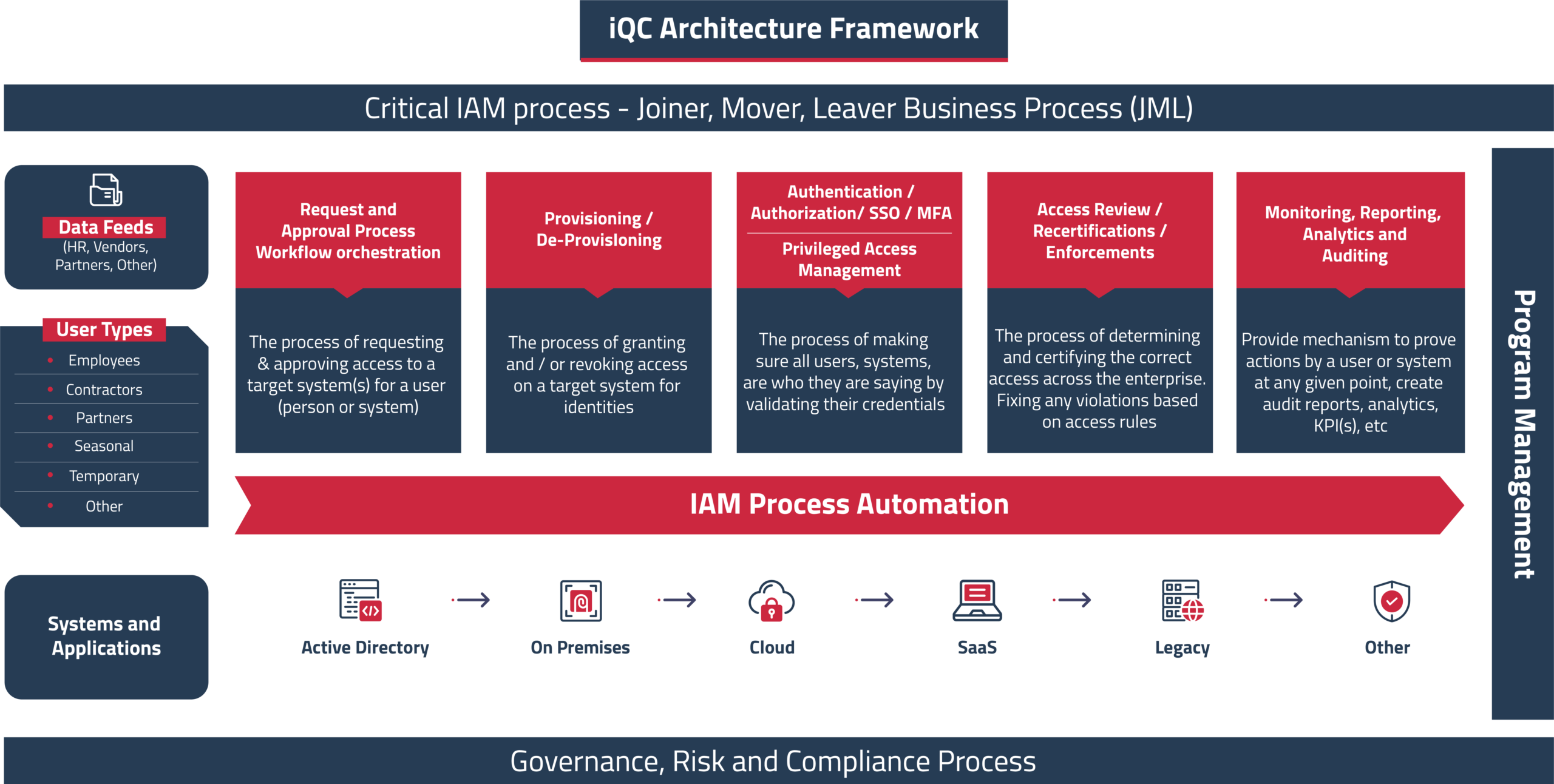
IAM Sample Architecture Framework and Review